You are the administrator of two Microsoft Windows 2000 computers. One computer is running Internet Information Services (IIS), and the other is running SQL Server 2000. Company partners need to connect by means of the Internet and query data stored on th
题目
You are the administrator of two Microsoft Windows 2000 computers. One computer is running Internet Information Services (IIS), and the other is running SQL Server 2000. Company partners need to connect by means of the Internet and query data stored on the SQL Server computer. Some of these partners have computers that do not use Microsoft operating systems or Web browsers.
You need to configure the IIS and SQL Server 2000 computers to allow access to data by means of the IIS virtual directory. IIS uses Basic Authentication to allow access to the virtual directory.
Only company partners should have access to the SQL Server computer by means of the Internet. The partners should not be allowed to make ad hoc queries. You want to be able to audit successful and failed logins to the SQL Server computer.
You want to allow the partners access to the SQL Server computer while keeping your security scheme as simple as possible. Which two actions should you take? (Each correct answer represents part of the solution. Choose two.)
A.Configure the IIS virtual directory to allow URL queries.
B.Configure the IIS virtual directory to allow template queries.
C.Create a new Windows user account. Create a corresponding Windows Authenticated login on the SQL Server computer. Configure the IIS virtual directory to always use this login when connecting to the SQL Server computer.
D.Create a Windows Authenticated login on the SQL Server computer for the IIS Internet Guest Account. Configure the IIS virtual directory to always use the Internet Guest Account when connecting to the SQL Server computer.
E.Create a Windows Authenticated login for each company partner on the SQL Server computer. Configure the IIS virtual directory to use Windows Integrated Authentication when connecting to the SQL Server computer.
相似考题
更多“You are the administrator of two Microsoft Windows 2000 computers. One computer is running Internet Information Services (IIS), and the other is running SQL Server 2000. Company partners need to connect by means of the Internet and query data stored on th”相关问题
-
第1题:
You are the administrator of a SQL Server 2000 computer. The server contains confidential information about contracts on which your company has placed bids.
Company policy requires that bid information be removed permanently from the database one year after the bid closes. You need to comply with this policy and minimize server overhead.
What should you do?
A.Create a Data Transformation Services (DTS) package to remove bids that have a closing data older than one year.
B.Create a trigger to delete any bids that have a closing data older than one year. Bind the trigger to the bids table for all INSERT, UPDATE, and DELETE events.
C.Create a stored procedure to delete any bids that have a closing data order than one year. Use SQL server agent to schedule the stored procedure to run every night.
D.Create a view that contains a WHERE clause to exclude bids that have a closing date older than one year.
正确答案:C
解析:Explanation:Thisscenariorequiresustoremoveoldinformationonaregularbasis.Firstwecreateastoredprocedurewhichremovesallrowswherethebidinformationdateisolderthanthecurrentdateminusoneyear.Thenweschedulethisproceduretoruneveryday.Wewouldthenbesuretoneverhaveanyrowsolderthanayearinthetable.Note:Storedproceduresalsoimproveperformanceasthestoredprocedureiscachedafteritisrun.ThisresultsinareductionofphysicalI/O.WecanfurtherreduceServeroverheadbyschedulingthestoredproceduretorunduringoff-peakhours.IncorrectAnswers:A:ADataTransformationServices(DTS)packageprovidesasetoftoolsthatallowsustoextract,transform,andconsolidatedatastoredinavarietyofformatsandindifferentlocationsintosingleormultipledestinationssupportedbyDTSconnectivity.Thissolutionisinappropriate,asthedataexistsontheserverandnotinnumerouslocationsandwouldthusbecorrectlyformattedforuseonaninstanceSQLServer2000.B:TriggersareaspecialtypeofstoredprocedurethatexecutesautomaticallywhenanUPDATE,INSERT,orDELETEstatementisrunagainstatableorview.Inthisscenariohowever,thedatestampofthedatainthedatabasemustbecheckedandthedatadeletedoneyearafterthebidhasclosed.Thiscannotbeaccomplishedthroughtheuseofconstraintsortriggers.D:Creatingaviewthatexcludesthebidsthathaveaclosingdateolderthanoneyeardoesnotaddressthecompanypolicythatrequiresthatbidinformationberemovedpermanentlyfromthedatabaseoneyearafterthebidcloses.Thisdatawillstillexistinthebasetables. -
第2题:
You are the administrator of two Microsoft Windows 2000 advanced server computers. On these servers, you are configuring a database that will store accounting information for your company.
The data must be available at all times. Interruptions in data connectivity should not last longer than five minutes. Any changes to the database should not require you to reconfigure the client computers.
How should you configure the database?
A.Configure the database on the two servers as a SQL Server 2000 cluster.
B.Configure the database on one server, and then configure a standby database on the second server.
C.Configure the database on each server. Use Microsoft Distributed Transaction Coordinator to keep the two servers perfectly synchronized.
D.Configure the database as a federated database, and then partition half the data on each server.
正确答案:A
解析:Explanation: SQL Server 2000 failover clustering provides high availability support by allowing us to configure one failover cluster to automatically, with no manual configuration, fail over to any other node in the failover cluster configuration. In this way, we minimize system downtime and provide high server availability during an operating system failure or a planned upgrade. Before SQL Server 2000 failover clustering can be set up, we must install Windows NT 4.0, Enterprise Edition, Windows 2000 Advanced Server or Windows 2000 Datacenter Server, and the Microsoft Cluster Service (MSCS).
In this scenario a cluster would be preferred to a standby server because it would be available immediately. A standby server on the other would require manual configuration and more time to become online.
Incorrect Answers:
B: A standby server would require you to reconfigure clients to allow it to connect to the standby server when the main server goes down. It would require at least several minutes of manual administration before the standby server would be operational. But the scenario requires that no reconfiguration of the client computers should be necessary. Therefore we should use a SQL Server 2000 cluster not a standby server.
Note: A standby server is a second server that contains a copy of the databases on the primary server and that can be brought online in the event of a primary server failure or due to scheduled maintenance on the primary server. This allows users to continue working with databases when the primary server becomes unavailable. When the primary server becomes available again, any changes to the standby server's copies of databases must be restored back to the primary server.
C: The Microsoft Distributed Transaction Coordinator coordinates distributed transactions, but would not increase availability.
Note: The Microsoft Distributed Transaction Coordinator (MS DTC) is a transaction manager that allows client applications to include several different sources of data in one transaction. MS DTC coordinates committing the distributed transaction across all the servers enlisted in the transaction.
An installation of SQL Server 2000 can participate in a distributed transaction by calling stored procedures on remote servers running SQL Server, automatically or explicitly promoting the local transaction to a distributed transaction and enlist remote servers in the transaction, and making distributed updates that update data on multiple OLE DB data sources. If these OLE DB data sources support the OLE DB distributed transaction interface, SQL Server 2000 can also enlist them in the distributed transaction. The MS DTC service coordinates the proper completion of the distributed transaction to ensure that either all of the updates on all the servers are made permanent, or, in the case of errors, all erased.
D: With Federated SQL Server 2000 servers, SQL Server 2000 databases can be spread across a group of autonomous database servers. These are capable of supporting the processing growth requirements of the largest Web sites and enterprise data-processing systems built with Microsoft Windows DNA, which divides the processing units of a data processing system into logical tiers. This however does not improve availability.
-
第3题:
You are the administrator of the Coho Vineyard network. The network consists of 10 Windows 2000 Advanced Server computers and 250 Windows 2000 Professional computers.
Your company has two domains cohovineyard.com and westcoastsales.com.
The company's intranet site is on a Windows 2000 Advanced Server computer named ServerA. ServerA is in the cohovineyard.com domain and is running Internet Information Services (IIS) and Microsoft Proxy Server 2.0
You want to configure the Windows 2000 Professional computers in the westcoastsales.com domain to access the intranet site. You want users to be able to connect to the intranet site by using the URL http://serverA rather than its fully qualified domain name.
What should you do?
A.Add cohovineyard.com to the Domain Suffix Search Order on the computers.
B.Add westcoastsales.com to the Domain Suffix Search Order on the computers.
C.Add westcoastsales.com to the exceptions list in the proxy server settings on the computers.
D.Configure the proxy server settings on the computers to bypass the proxy server for intranet addresses.
正确答案:A
解析:Explanation: ServerA is located in the domain cohovineyard.com. If you add cohovineyard.com to the domain suffix then http://ServerA will translate to http://ServerA.cohovineyard.com, which would resolve this problem. This configuration can be done by opening TCP/IP properties, selecting the Advanced button, selecting the DNS tab, selecting 'Append these DNS Suffixes (inorder)', selecting Add, and entering cohovineyard.com
Incorrect Answers:
B: ServerA is located in the cohovineyard.com domain, not in the westcoastsales.com domain.
C: The domain suffix must be used to configure the connection, and not the proxy server settings.
D: By configuring the proxy setting to bypass the proxy server for intranet addresses, you would prevent intranet access from accessing external DNS servers. It also would not allow users to use the shorthand URL of http://serverA. -
第4题:
You are the network administrator for Company. Company’s network consists of 200 Windows 2000 Professional computers. CompanyW1 is a Windows 2000 Server computer that hosts Company’s intranet site. CompanyP1 is a computer running Microsoft Proxy Server that is used by all computers on the network to access the Internet. You discover that CompanyP1 is experiencing performance degradation due to large number of requests to authenticate with the proxy server. You want to minimize the number of authentication requests to the proxy server. What should you do on each computer?()
- A、Configure the proxy server settings to have a Secure proxy address of CompanyP1.
- B、Configure the proxy server settings to bypass the proxy server for local addresses.
- C、Add CompanyW1 to the Local intranet zone.
- D、Add the CompanyW1 to the list of trusted sites.
正确答案:B -
第5题:
You are the administrator of a SQL Server 2005 computer named SQL1. All servers run Microsoft Windows Server 2003 and belong to a Microsoft Active Directory domain. The companys written security policy mandates strong passwords for all domain, local, and application accounts. The appropriate domain password policy has been deployed through the use of a Group Policy object (GPO). Many of the company’s computers run MS-DOS-based or UNIX-based operating systems. These computers require varying levels of access to a database named Services on SQL1. You need to ensure that these computers can access the Services database without violating the company’s written security policy. What should you do?()
- A、Create a domain account for each of the company’s users. Provide each domain account with access to SQL1 and the Services database.
- B、Create a local logon account on SQL1 for each of the company’s users. Provide each logon account with access to SQL1 and the Services database.
- C、Create a SQL Server logon account for each of the company’s users. Enable the Enforce password policy option for each logon account. Provide each logon account with access to the Services database.
- D、Configure a virtual directory through Internet Information Services (IIS) for access to SQL1. Direct users to the virtual directory for data access.
- E、Create one SQL Server logon account for all of the company’s computers running MS-DOS or UNIX-based operating systems. Enable the Enforce password policy option for users’ accounts. Provide the logon accounts with access to the Services database.
正确答案:C -
第6题:
You need to design the consolidation plan for SQL1, SQL2, and SQL3. You need to identify the appropriate combination of SQL Server instances and SQL Server 2005 computers that are needed to fulfill the company’s consolidation plans and security requirements.Which combination should you use?()
- A、one SQL Server 2005 computer with one instance
- B、two SQL Server 2005 computers, each with two instances
- C、two SQL Server computers, one with one instance and one with three instances
- D、one SQL Server 2005 computer with two instances
正确答案:D -
第7题:
You are a network administrator for your company. You manage a computer named Server6 that runs Windows Server 2003 with the default settings.You install Terminal Services on Server6. You attempt to connect to Server6 by using the URLhttp://Server6/Tsweb. You cannot connect to Server6. You need to be able to access Terminal Services on Server6 by using Internet Explorer 6.0.Which two actions should you perform? ()(Each correct answer presents part of the solution. Choose two.)
- A、Create a new Web site named Tsweb.
- B、Create a new virtual directory named Tsweb.
- C、Install IIS.
- D、Install the Remote Administration IIS subcomponent.
- E、Install the Remote Desktop Web Connection IIS subcomponent.
正确答案:C,E -
第8题:
You work as a network Exchange administrator at Company.com.The Company.com network currently consists of a single Active Directory forest containing a single domain named Company.com.The Company.com organization makes use of Microsoft Exchange Server as their messaging solution.During the course of the business week you receive instruction from Company.com to install the Microsoft Exchange Server 2010 management tools on a computer running Microsoft Windows 7. What should you do?()
- A、You should consider having the Net.TCP Port Sharing service set to Automatic.
- B、You should consider having Microsoft .NET Framework 3.5.1 and the Internet Information Services (IIS) 6.0 Management console installed first.
- C、You should consider having the Telnet Client installed first.
- D、You should consider having the Exchange Best Practices Analyzer run first.
正确答案:B -
第9题:
Certkiller .com has a software evaluation lab. There is a server in the evaluation lab named as CKT. CKT runs Windows Server 2008 and Microsoft Virtual Server 2005 R2. CKT has 200 virtual servers running on an isolated virtual segment to evaluate software. To connect to the internet, it uses physical network interface card. Certkiller .com requires every server in the company to access Internet. Certkiller .com security policy dictates that the IP address space used by software evaluation lab must not be used by other networks. Similarly, it states the IP address space used by other networks should not be used by the evaluation lab network. As an administrator you find you that the applications tested in the software evaluation lab need to access normal network to connect to the vendors update servers on the internet. You need to configure all virtual servers on the CKT server to access the internet. You also need to comply with company’s security policy. Which two actions should you perform to achieve this task()
- A、Trigger the Virtual DHCP server for the external virtual network and run ipconfig/renew command on each virtual server
- B、On CKT’s physical network interface, activate the Internet Connection Sharing (ICS)
- C、Use Certkiller .com intranet IP addresses on all virtual servers on CKT.
- D、Add and install a Microsoft Loopback Adapter network interface on CKT. Use a new network interface and create a new virtual network.
- E、None of the above
正确答案:A,D -
第10题:
You are a professional level SQL Server 2005 database administrator in an international corporation named Wiikigo. You are experienced in implementing high-availability solutions, monitoring the database server, and design deployment. In the company, you major job is the deployment, maintenance and support of Microsoft SQL Server 2005. You work as the administrator of a SQL Server 2005 computer, and the computer is named SQL1. Microsoft Windows Server 2003 is run by all servers. All the servers belong to a Microsoft Active Directory domain. According to the company written security policy, strong passwords are mandated for all domain, local, and application accounts. The company utilizes a Group Policy object (GPO) to deploy the proper domain password policy. MS-DOS-based or UNIX-based operating systems are run by many of the company’s computers. Varying levels of access to a database named Services on SQL1 is requested by the computers. Since you are the database administrator, you are required to confirm that the Services database can be accessed by these computers. And the company’s written security policy should not be violated. Which action should be performed by you?()
- A、A domain account should be created for each of the company’s users. And then, each domain account should be offered with access to SQL1 and the Services database.
- B、A local logon account should be created on SQL1 for each of the company’s users. And then, each logon account should be offered with access to SQL1 and the Services database.
- C、One SQL Server logon account should be created for all of the company’s computers running MS-DOS or UNIX-based operating systems. And then, the Enforce password policy option should be enabled for users’ accounts. At last, the logon accounts should be provided with access to the Services database.
- D、A SQL Server logon account should be created for each of the company’s users. And then, the Enforce password policy option should be enabled for each logon account. At last, each logon account should be offered with access to the Services database.
- E、A virtual directory should be configured through Internet Information Services (IIS) for access to SQL1. And then, users should be directed to the virtual directory for data access.
正确答案:D -
第11题:
单选题You work as a network Exchange administrator at Company.com.The Company.com network currently consists of a single Active Directory forest containing a single domain named Company.com.The Company.com organization makes use of Microsoft Exchange Server as their messaging solution.During the course of the business week you receive instruction from Company.com to install the Microsoft Exchange Server 2010 management tools on a computer running Microsoft Windows 7. What should you do?()AYou should consider having the Net.TCP Port Sharing service set to Automatic.
BYou should consider having Microsoft .NET Framework 3.5.1 and the Internet Information Services (IIS) 6.0 Management console installed first.
CYou should consider having the Telnet Client installed first.
DYou should consider having the Exchange Best Practices Analyzer run first.
正确答案: A解析: 暂无解析 -
第12题:
多选题You are a database administrator for your company. You are configuring a new SQL Server 2005 computer named SQL1. SQL1 will run Reporting Services. It will also be configured to automatically perform database backups and other maintenance tasks. There are no other SQL Server computers in the network environment. All access to SQL1 will be made by using SQL1s DNS name. You need to disable any unnecessary services on SQL1. Which service or services should you disable?()AInternet Information Services
BSQL Server Browser
CSQL Server Agent
DMicrosoft Distributed Transaction Coordinator
正确答案: B,D解析: 暂无解析 -
第13题:
You are the administrator of a SQL server computer. The server is running SQL Server 6.5 and SQL Server 7.0.
You install a named instance of SQL Server 2000, and then run the SQL server upgrade wizard. On the database selection screen, some of the SQL Server 6.5 databases are not listed.
You cancel the SQL Server upgrade wizard.
You need to ensure that the SQL Server 6.5 databases are listed in the wizard. What should you do?
A.Uninstall SQL Server 7.0, and then rerun the SQL Server upgrade wizard.
B.Run the Microsoft SQL Server-switch application, and then rerun the SQL Server upgrade wizard.
C.Create a data transformation services package that imports the databases from SQL Server 6.5 to SQL Server 2000, and then execute the package.
D.Uninstall SQL Server 2000, and then reinstall SQL Server 2000 as the default instance.
正确答案:D
解析:Explanation:ToruntheSQLServerUpgradeWizard,youmusthaveadefaultinstanceofMicrosoftSQLServer2000installedonyourcomputer.IncorrectAnswers:A:ItisnotnecessarytouninstallSQLServer7.0.JustinstallSQLServer2000asthedefaultinstance.WecannotruntheSQLServerupgradewizardunlessSQLServer2000isinstalled.B:ToruntheSQLServerUpgradeWizard,youmusthaveadefaultinstanceofMicrosoftSQLServer2000installedonyourcomputer.C:WewanttoensurethattheSQLServer6.5databasesarelistedintheSQLServer2000installationwizard.TocreateDTStransformationpackagesthatupgradeSQLServer6.5databaseestoSQLServer2000databaseswemustinstallSQLServer2000first. -
第14题:
You are the administrator of a SQL Server 2000 computer. Your company uses the server to store service contract information for its customers.
You are also the administrator of Oracle relational database management system (RDBMS) server.
This server is used to store your company’s financial information. The financial information is updated frequently throughout the day.
You need to create a series of reports that combine the service contract information and the financial information. These reports will be updated several times a day.
You want to create reports on the SQL Server computer by using the minimum amount of disk space.
What should you do?
A.Set up SQL server replication to replicate the data from the oracle server to the SQL server computer.
B.Set up the oracle server as a linked server. Create a view that joins the service contract information and the financial information.
C.Set up data transformation services (DTS) package that imports and transforms the database from the oracle server to the SQL server computer. Use SQL server agent to execute the DTS package throughout the day as needed.
D.Set up Microsoft ActiveX script. that connects to the oracle server and imports the financial information into SQL server temporary table. Create a view that joins the service contract information and the temporary table.
正确答案:B
解析:Explanation: SQL Server 2000 permits the creation of links to OLE DB data sources called linked servers. After linking to an OLE DB data source, it is possible to reference rowsets from the OLE DB data sources as tables in Transact-SQL statements and to pass commands to the OLE DB data sources and include the resulting rowsets as tables in Transact-SQL statements.
Each distributed query can reference multiple linked servers and can perform. either update or read operations against each individual linked server. A single distributed query can perform. read operations against some linked servers and update operations against other linked servers. The Microsoft OLE DB Provider for Oracle allows distributed queries to query data in Oracle databases.
Incorrect Answers:
A: Replication allows for the coping, distribution, and modification of data across an enterprise. This involves the copying of database data from one server to another. This is not the best solution in this scenario as this will require frequent replication because the reports must be updated several times a day.
C: Data Transformation Services is a set of graphical tools and programmable objects that allows for the extraction, transformation, and consolidation of data from disparate sources into single or multiple destinations. In this scenario, however, the Oracle database needs to be included in a query. Hence, Data Transformation Services are inappropriate.
D: Microsoft ActiveX scripts can be used to add functionality to Data Transformation Services packages, which is a set of graphical tools and programmable objects that allows for the extraction, transformation, and consolidation of data from disparate sources into single or multiple destinations. In this scenario, however, the Oracle database needs to be included in a query. Hence, Data Transformation Services are inappropriate.
-
第15题:
You are the administrator of Microsoft Windows 2000 computer. You are preparing to install SQL Server 2000 on the computer.
Your company contains a variety of client computers that will connect to the SQL server 2000 computer by using a specific Net-Library, as shown in the following table.
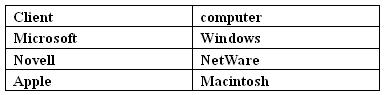
You need to allow the client computers to connect to the SQL Server 2000 computer. You also want to minimize the number of configuration changes required on the client computers.
Which three actions should you take? (Each correct answer presents part of the solution. Choose three)
A. Install SQL Server 2000 as a named instance.
B. Install SQL Server 2000 as the default instance.
C. Configure the new instance for Mixed Mode Authentication.
D. Configure the new instance for Windows Authentication.
E. Configure the server to use the Named Pipes, IPX/SPX, and TCP/IP Net-Libraries.
F. Configure the server to use the Multiprotocol Net-Library.
正确答案:BCE
B,C,E 解析:Explanation:
B: We need to use a default instance of SQL Server in order to allow all the different clients to connect.
C: The client computers in this scenario will be running Windows 98, Novel NetWare and Apple Macintosh. SQL Server Authentication is required as these operating systems are not supported by Windows Authentication, however, the use of SQL Server Authentication is offered only for backward compatibility, hence we need to implement Mixed Mode Authentication.
E: By using specific communication protocols, and not the Multiprotocol Net-Library, performance would be better. Every extraneous protocol adds overhead.
Note: Configuring Net-Libraries has been simplified for applications using the SQL Server 2000 client connectivity components. Selecting the client protocols to be installed on the application computer must be done during setup, and selecting the server protocols to be enabled on the instance of SQL Server 2000 must be done during the SQL Server 2000 setup. No other configuration is required. Once setup, a client can connect to any instance of SQL Server 2000 by specifying the network name of the database computer and the instance name.
Note: SQL Server 2000 can operate in either Windows Authentication mode, which allows a user to connect through a Windows NT 4.0 or Windows 2000 user account; Mixed mode, which allows users to connect to an instance of SQL Server 2000 by using either Windows Authentication or SQL Server Authentication.
Furthermore, users who connect through a Windows NT 4.0 or Windows 2000 user account can make use of trusted connections in either Windows Authentication mode or Mixed mode. When a user connects to SQL Server 2000 with a nontrusted connection, SQL Server 2000 performs the authentication itself by checking if a SQL Server login account has been created and if the supplied password is correct. SQL Server Authentication is also used for backward compatibility because applications written for SQL Server 7.0 or earlier may require the use of SQL Server logins and passwords. In addition, SQL Server Authentication is required when an instance of SQL Server is running on Windows 98 because Windows Authentication mode is not supported on Windows 98.
Incorrect Answers:
A: The Multiprotocol Net-Library can only be used to connect to a default instance of SQL Server 2000 as it does not support named instances of SQL Server 2000 or server enumeration.
D: As client computers will be running Windows 98, Novel NetWare and Apple Macintosh, we cannot use Windows Authentication as these operating systems are not supported by Windows Authentication.
Note: Windows Authentication mode allows a user to connect through a Windows NT 4.0 or Windows 2000 user account and makes use of trusted connections. When a user connects to SQL Server 2000 a nontrusted connection, SQL Server 2000 performs the authentication itself by checking if a SQL Server login account has been created and if the supplied password is correct. Mixed mode allows users to connect to an instance of SQL Server 2000 by using either Windows Authentication or SQL Server Authentication.
F: The Multiprotocol Net-Library is used to support the different protocol that the clients use. This provides easy of administration. However, since unused protocols are installed, it also introduces overhead. This is not the best solution.
Note: The Multiprotocol Net-Library allows for the automatic selection of available network protocols to communicate with an instance of SQL Server 2000. This is convenient for connecting to multiple servers running different network protocols without having to reconfigure the client connection for each server. If the client and server Net-Libraries for TCP/IP Sockets, NWLink IPX/SPX, or Named Pipes are installed on the client and server, the Multiprotocol Net-Library will automatically choose the first available network protocol to establish a connection.
The Multiprotocol Net-Library can only be used to connect to a default instance of SQL Server 2000 as it does not support named instances of SQL Server 2000 or server enumeration.
-
第16题:
Your application must access data that is located on two SQL Server 2005 computers. One of these servers is named SQL1 and the other is SQL2. You have permissions to create a stored procedure on SQL1 to support your application. However,on SQL2 you only have permissions to select data. You write the stored procedure on SQL1. The stored procedure accesses SQL2 by using the OPENQUERY Transact-SQL statement. However,the query fails when executed.You need to troubleshoot the cause of the error. What should you do?()
- A、Join the two servers by using the four-part syntax of server.database.schema.table.
- B、Reference SQL2 by using an alias.
- C、Add SQL2 as a remote server to SQL1.
- D、Add SQL2 as a linked server to SQL1.
正确答案:D -
第17题:
You are the administrator of the Coho Vineyard network. The network consists of 10 Windows 2000Advanced Server computers and 250 Windows 2000 Professional computers.Your company has two domains cohovineyard.com and westcoastsales.com.The company’s intranet site is on a Windows 2000 Advanced Server computer named Server A. ServerA is in the cohovineyard.com domain and is running Internet Information Services and Microsoft Proxy Server2.0 You want to configure the Windows 2000 Professional computers in the westcoastsales.com domain to ccess the intranet site. You want users to be able to connect to the intranet site by using the URL http://serverA rather than its fully qualified domain name. What should you do?()
- A、Add cohovineyard.com to the domain suffix search order on the computers.
- B、Add westcoassales.com to the domain suffix search orders on the computers.
- C、Add westcoassales.com to the exceptions list in the Proxy server settings on the computers.
- D、Configure the Proxy server settings on the computers to bypass the proxy server for intranet addresses.
正确答案:A -
第18题:
You are the network administrator for your company. The network consists of a single Active Directory domain. All servers run Windows Server 2003. All client computers run either Windows XP Professional or Windows 2000 Professional. All client computer accounts are located in an organizational unit (OU) named Workstation. A written company policy states that the Windows 2000 Professional computers must not use offline folders. You create a Group Policy object (GPO) to enforce this requirement. The settings in the GPO exist for both Windows 2000 Professional computers and Windows XP Professional computers. You need to configure the GPO to apply only to Windows 2000 Professional computers. What are two possible ways to achieve this goal?()
- A、 Create a WMI filter that will apply the GPO to computers that are running Windows 2000 Professional.
- B、 Create a WMI filter that will apply the GPO to computers that are not running Windows XP Professional.
- C、 Create two OUs under the Workstation OU. Place the computer accounts for the Windows XP Professional computers in one OU, and place the computer accounts for the Windows 2000 Professional computers in the other OU. Link the GPO to the Workstation OU.
- D、 Create a group that includes the Windows XP Professional computers. Assign the group the Deny - Generate Resultant Set of Policy(Logging) permission.
- E、 Create a group that includes the Windows 2000 Professional computers. Assign the group the Deny - Apply Group Policy permission.
正确答案:A,B -
第19题:
You are a professional level SQL Server 2005 database administrator in an international corporation named Wiikigo. You are experienced in implementing high-availability solutions, monitoring the database server, and design deployment. In the company, you major job is the deployment, maintenance and support of Microsoft SQL Server 2005. You work a database administrator for your company. There is a Data Transformation Services (DTS) package, and the DTS package is stored in SQL Server 2000. And you plans to have the SQL Server 2000 migrated into SQL Server 2005. The DTS package dynamically configures precedence constraints by utilizing complex Microsoft Visual Basic Scripting Edition (VBScript). The SQL Server 2005 Package Migration Wizard is run by you, but the wizard cannot convert the package from SQL Server 2000 to SQL Server 2005. You are required to make sure that the DTS package runs in SQL Server 2005. And the package should be run in the shortest time. Which action should be utilized?()
- A、The SQL Server 2000 Data Transformation Services (DTS) package should be wrapped in an Execute DTS 2000 Package task.
- B、The SQL Server 2000 Data Transformation Services (DTS) package should be manually recreated as a SQL Server Integration Services (SSIS) package.
- C、The SQL Server 2000 Data Transformation Services (DTS) task should be configured to not utilize precedence constraints. Then, the SQL Server 2005 Package Migration Wizard should be run again.
- D、The SQL Server 2005 Package Migration Wizard should be run. And when the upgrade fails, a Transfer SQL Server Objects task should be run.
正确答案:A -
第20题:
You are the network administrator for. The network consists of a single Active Directory forest that contains two domains. You have not modified the default Active Directory site configurations. The functional level of both domains is Windows 2000 native. Servers run either Windows Server 2003 or Windows 2000 Server. TestKing's internal domain is named testking.local. Testking's external domain is named . The external domain is accessed only by TestKing's business partners. You install a Windows Server 2003 computer named Testking7 in the domain. You install and configure Terminal Services on Testking7. Testking7 is configured as a member server in the domain. You install a secure database application on Testking7 that will be accessed by TestKing's business partnersA few months later, users report that they can no longer establish Terminal Services session to Testking7. You verify that only the default ports for HTTP, HTTPS, and Terminal Services on your firewall are open to the Internet. You need to ensure that TestKing's business partners can establish Terminal Services sessions to Testking7. What are two possible ways to achieve this goal?() (Each correct answer presents a complete solution. Choose two)
- A、Install Terminal Services Licensing on a Windows 2000 Server computer in testking.local. Configure the computer as an Enterprise License Server.
- B、Install Terminal Services Licensing on a Windows 2000 Server computer in extranet.testking.com. Configure the computer as an Enterprise License Server
- C、Install Terminal Services Licensing on a Windows Server 2003 computer in extranet.testking.com. Configure the computer as an Enterprise License Server.
- D、Install Terminal Services Licensing on a Windows Server 2003 computer in testking.local. Configure the computer as an Enterprise License Server.
- E、Instruct TestKing's business partners to connect by using the Terminal Services Advanced Client (TSAC) over HTTPS.
正确答案:B,C -
第21题:
You want to connect to your branch office printer through the browser. Your Windows 2000 Professional computer is running Peer Web Server. You were told the share name of the printer is HPColorL. You are unable to see it when you type its URL. What do you need to do to connect to this printer? ()
- A、Double-click the connect hotspot in the left pane of the printer's dialog box to view the printer.
- B、Ask the branch office administrator to reinstall the printer by using its URL as the port.
- C、Install Internet Explorer 3.0 or higher on your Windows 2000 Professional.
- D、Ask the administrator at the branch office to install IIS on the branch server.
正确答案:D -
第22题:
You are a database administrator for your company. You are configuring a new SQL Server 2005 computer named SQL1. SQL1 will run Reporting Services. It will also be configured to automatically perform database backups and other maintenance tasks. There are no other SQL Server computers in the network environment. All access to SQL1 will be made by using SQL1s DNS name. You need to disable any unnecessary services on SQL1. Which service or services should you disable?()
- A、Internet Information Services
- B、SQL Server Browser
- C、SQL Server Agent
- D、Microsoft Distributed Transaction Coordinator
正确答案:B,D -
第23题:
单选题You are a professional level SQL Server 2005 database administrator in an international corporation named Wiikigo. You are experienced in implementing high-availability solutions, monitoring the database server, and design deployment. In the company, you major job is the deployment, maintenance and support of Microsoft SQL Server 2005. You work as the administrator of a SQL Server 2005 computer, and the computer is named SQL1. Microsoft Windows Server 2003 is run by all servers. All the servers belong to a Microsoft Active Directory domain. According to the company written security policy, strong passwords are mandated for all domain, local, and application accounts. The company utilizes a Group Policy object (GPO) to deploy the proper domain password policy. MS-DOS-based or UNIX-based operating systems are run by many of the company’s computers. Varying levels of access to a database named Services on SQL1 is requested by the computers. Since you are the database administrator, you are required to confirm that the Services database can be accessed by these computers. And the company’s written security policy should not be violated. Which action should be performed by you?()AA domain account should be created for each of the company’s users. And then, each domain account should be offered with access to SQL1 and the Services database.
BA local logon account should be created on SQL1 for each of the company’s users. And then, each logon account should be offered with access to SQL1 and the Services database.
COne SQL Server logon account should be created for all of the company’s computers running MS-DOS or UNIX-based operating systems. And then, the Enforce password policy option should be enabled for users’ accounts. At last, the logon accounts should be provided with access to the Services database.
DA SQL Server logon account should be created for each of the company’s users. And then, the Enforce password policy option should be enabled for each logon account. At last, each logon account should be offered with access to the Services database.
EA virtual directory should be configured through Internet Information Services (IIS) for access to SQL1. And then, users should be directed to the virtual directory for data access.
正确答案: B解析: 暂无解析
