The network security policy for Ezonexam requires that only one host be permitted to attach dynamically to each switch interface. If that policy is violated, the interface should be automatically disabled. Which two commands must the Ezonexam network admi
题目
The network security policy for Ezonexam requires that only one host be permitted to attach dynamically to each switch interface. If that policy is violated, the interface should be automatically disabled. Which two commands must the Ezonexam network administrator configure on the 2950 Catalyst switch to meet this policy? (Choose two)
A.SWEzonexam1(config-if)# switchport port-security maximum 1
B.SWEzonexam1(config)# mac-address-table secure
C.SWEzonexam1(config)# access-list 10 permit ip host
D.SWEzonexam1(config-if)# switchport port-security violation shutdown
E.SWEzonexam1(config-if)# ip access-group 10
相似考题
更多“The network security policy for Ezonexam requires that only one host be permitted to attach dynamically to each switch interface. If that policy is violated, the interface should be automatically disabled. Which two commands must the Ezonexam network admi”相关问题
-
第1题:
Split horizon has been enabled within the Ezonexam routed network. Which one of the following statements best explains the split horizon rule?
A.Only routers can split boundaries (horizons) between networks in separate AS numbers.
B.Each AS must keep routing tables converged to prevent dead routes from being advertised across boundaries.
C.Once a route is received on an interface, advertise that route as unreachable back out the same interface.
D.Information about a route should never be sent back in the direction from which the original update came.
E.None of the above
正确答案:D
解析:Explanation:
The split horizon rule states:
* Never advertise a route out of the interface through which you learned it.
For instance, in Figure 4a below, if Router One is connected to Routers Two and Three through a single multipoint interface (such as Frame. Relay), and Router One learned about Network A from Router Two, it will not advertise the route to Network A back out the same interface to Router Three. Router one assumes that Router Three would learn about Network A directly from Router Two.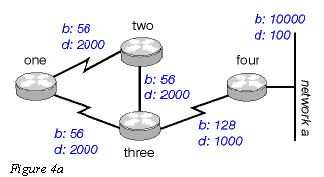
Incorrect Answers:
A: There is no such requirement
B: Distance vector protocols updates routing table at regular intervals instead of Topology changes
C: This is the definition of the poison reverse rule, not the split horizon rule.
-
第2题:
A network vulnerability scanner is part of which critical element of network and system security?()A. host security
B. perimeter security
C. security monitoring
D. policy management
参考答案:C
-
第3题:
Which two statements about the configuration of the switch interface are correct (Choose two)()。A.The switchport belongs only to VLAN 2
B.Interface fa0/0 will be in both VLAN 1 (by default) and VLAN 2
C.The exhibit shows interface fa0/0 to be dynamically mapped to VLAN 2
D.A network host can be connected to this interface
参考答案:A, D
-
第4题:
You work as the IT professional in an international company which is named Wiikigo. You are experiencedin implementing and administering a network operating system. You are specialized in deploying servers,configuring Windows Server 2008 Terminal services and network application services, and configuring aweb services infrastructure. There is a server named S01 that runs Windows Server 2008 and Hyper-V inyour company. Three virtual machines are hosted on S01. According to the requirement of company policy,the virtual machines must not connect to the company network. All of the virtual machines need to beconfigured to connect to each other. You must meet the company policy. Which should you do?()
- A、The Connection should be set to Host for the network interface card.
- B、The Connection should be set to None for the network interface card.
- C、You should choose the Not connected option for each virtual machine.
- D、The Enable virtual LAN identification option should be enabled for each virtual machine.
正确答案:A,D -
第5题:
A network vulnerability scanner is part of which critical element of network and system security?()
- A、host security
- B、perimeter security
- C、security monitoring
- D、policy management
正确答案:C -
第6题:
Your security policy requires that users authenticating to the Junos Pulse Access Control Service are connecting from a domain member endpoint on the internal corporate network.Which set of role access restrictions must you configure to enforce this security policy?()
- A、Source IP and browser
- B、Source IP and certificate
- C、Certificate and Host Checker
- D、Host Checker and source IP
正确答案:D -
第7题:
Your company uses Network Access Protection (NAP) to enforce policies on client computers taht connect to the network. Client computers run Windows Vista. A Group Policy is used to configure client computers to obtain updates from WSUS. Company policy requires that updates labeled important and Critical must be applied before client computers can access network resources. You need to ensure that client computers meet the company policy requirement. What should you do()
- A、 Enable automatic updates on each client
- B、 enable the Security Center on each client
- C、 Quarantine clients that do nto have all availible security updates installed
- D、 Disconnect the remote connection until the required updates are installed.
正确答案:C -
第8题:
ou are the network administrator for your company. The network consists of a single Active Directory domain. All servers run Windows Server 2003. All client computers run Windows XP Professional.Two of the servers on the network contain highly confidential documents. The company’s written security policy states that all network connections with these servers must be encrypted by using an IPSec policy.You place the two servers in an organizational unit (OU) named SecureServers. You configure a Group Policy object (GPO) that requires encryption for all connections. You assign the GPO to the SecureServers OU. You need to verify that users are connecting to the two servers by using encrypted connections. What should you do?()
- A、Run the net view command.
- B、Run the gpresult command.
- C、Use the IP Security Monitor console.
- D、Use the IPSec Policy Management console.
正确答案:C -
第9题:
Your company has a server named Server1 that runs Windows Server 2008 and Microsoft Hyper-V. Server1 hosts three virtual machines. Company policy states that the virtual machines must not connect to the company network. You need to configure all of the virtual machines to connect to each other. You must meet the company policy. Which two actions should you perform?()
- A、Select the Not connected option for each virtual machine.
- B、Enable the Enable virtual LAN identification option for each virtual machine.
- C、Set the Connection to Host for the network interface card.
- D、Set the Connection to None for the network interface card.
正确答案:B,C -
第10题:
多选题You work as the IT professional in an international company which is named Wiikigo. You are experiencedin implementing and administering a network operating system. You are specialized in deploying servers,configuring Windows Server 2008 Terminal services and network application services, and configuring aweb services infrastructure. There is a server named S01 that runs Windows Server 2008 and Hyper-V inyour company. Three virtual machines are hosted on S01. According to the requirement of company policy,the virtual machines must not connect to the company network. All of the virtual machines need to beconfigured to connect to each other. You must meet the company policy. Which should you do?()AThe Connection should be set to Host for the network interface card.
BThe Connection should be set to None for the network interface card.
CYou should choose the Not connected option for each virtual machine.
DThe Enable virtual LAN identification option should be enabled for each virtual machine.
正确答案: B,D解析: 暂无解析 -
第11题:
单选题Your security policy requires that users authenticating to the Junos Pulse Access Control Service are connecting from a domain member endpoint on the internal corporate network.Which set of role access restrictions must you configure to enforce this security policy?()ASource IP and browser
BSource IP and certificate
CCertificate and Host Checker
DHost Checker and source IP
正确答案: B解析: 暂无解析 -
第12题:
多选题Which two statements about the configuration of the switch interface are correct (Choose two)()。AThe switchport belongs only to VLAN 2
BInterface fa0/0 will be in both VLAN 1 (by default) and VLAN 2
CThe exhibit shows interface fa0/0 to be dynamically mapped to VLAN 2
DA network host can be connected to this interface
正确答案: D,C解析: 暂无解析 -
第13题:
The Ezonexam network administrator issues the ping 192.168.2.5 command and successfully tests connectivity to a host that has been newly connected to the network. Which protocols were used during the test? (Choose two)
A.ARP
B.CDP
C.DHCP
D.DNS
E.ICMP
正确答案:AE
解析:Explanation:ARPfindsthehardwareaddressofahostfromaknownIPaddress.Here'showitworks:whenIPhasadatagramtosend,itmustinform.aNetworkAccessprotocol,suchasEthernetorTokenRing,ofthedestination'shardwareaddressonthelocalnetwork.(Ithasalreadybeeninformedbyupper-layerprotocolsofthedestination'sIPaddress.)IfIPdoesn'tfindthedestinationhost'shardwareaddressintheARPcache,itusesARPtofindthisinformation.ICMPworksattheNetworklayerandisusedbyIPformanydifferentservices.ICMPisamanagementprotocolandmessagingserviceproviderforIP.ItsmessagesarecarriedasIPdatagrams.RFC1256isanannextoICMP,whichaffordshosts'extendedcapabilityindiscoveringroutestogateways.Periodically,routeradvertisementsareannouncedoverthenetwork,reportingIPaddressesfortherouter'snetworkinterfaces.Hostslistenforthesenetworkinfomercialstoacquirerouteinformation.Aroutersolicitationisarequestforimmediateadvertisementsandmaybesentbyahostwhenitstartsup. -
第14题:
The network security policy requires that only one host be permitted to attach dynamically to each switch interface. If that policy is violated, the interface should shut down. Which two commands must the network administrator configure on the 2950 Catalyst switch to meet this policy?()
A. Switch1(config-if)# switchport port-security maximum 1
B. Switch1(config)# mac-address-table secure
C. Switch1(config)# access-list 10 permit ip host
D. Switch1(config-if)# switchport p ort-security violation shutdown
E. Switch1(config-if)# ip access-group 10
参考答案:A, D
-
第15题:
The network security policy requires that only one host be permitted to attach dynamically to each switch interfacE.If that policy is violated, the interface should shut down. Which two commands must the network administrator configure on the 2950 Catalyst switch to meet this policy? ()
- A、Switch1(config-if)# switchport port-security maximum 1
- B、Switch1(config)# mac-address-table secure
- C、Switch1(config)# access-list 10 permit ip host
- D、Switch1(config-if)# switchport port-security violation shutdown
- E、Switch1(config-if)# ip access-group 10
正确答案:A,D -
第16题:
The network security policy requires that only one host be permitted to attach dynamically to each switch interface. If that policy is violated, the interface should shut down. Which two commands must the network administrator configure on the 2950 Catalyst switch to meet this policy (Choose two.)()。
- A、Switch1(config-if)# switchport port-security maximum 1
- B、Switch1(config)# mac-address-table secure
- C、Switch1(config)# access-list 10 permit ip host
- D、Switch1(config-if)# switchport port-security violation shutdown
- E、Switch1(config-if)# ip access-group 10
正确答案:A,D -
第17题:
The network security policy requires that only one host be permitted to attach dynamically to each switch interface. If that policy is violated, the interface should shut down. Which two commands must the network administrator configure on the 2950 Catalyst switch to meet this policy?()
- A、TestKing1(config-if)# switchport port-security maximum 1
- B、TestKing1(config)# mac-address-table secure
- C、TestKing1(config)# access-list 10 permit ip host
- D、TestKing1(config-if)# switchport port-security violation shutdown
- E、TestKing1(config-if)# ip access-group 10
正确答案:A,D -
第18题:
Which two statements are true regarding the system-default security policy [edit security policies default-policy]?()(Choose two.)
- A、Traffic is permitted from the trust zone to the untrust zone.
- B、Intrazone traffic in the trust zone is permitted.
- C、All traffic through the device is denied.
- D、The policy is matched only when no other matching policies are found.
正确答案:C,D -
第19题:
You are the network administrator for your company. The network consists of a single Active Directory domain. The company has an internal network and a perimeter network. The internal network is protected by a firewall. Application servers on the perimeter network are accessible from the Internet. You are deploying 10 Windows Server 2003 computers in application server roles. The servers will be located in theperimeter network and will not be members of the domain. The servers will host only publicly available Web pages. The network design requires that custom security settings must be applied to the application servers. These custom security settings must be automatically refreshed every day to ensure compliance with the design. You create a custom security template named Baseline1.inf for the application servers. You need to comply with the design requirements. What should you do? ()
- A、 Import Baseline1.inf into the Default Domain Policy Group Policy object (GPO).
- B、 Create a task on each application server that runs Security and Configuration Analysis with Baseline1.inf every day.
- C、 Create a task on each application server that runs the secedit command with Baseline1.inf every day.
- D、 Create a startup script in the Default Domain Policy Group Policy object (GPO) that runs the secedit command with Baseline1.inf.
正确答案:C -
第20题:
Your network consists of a single Active Directory forest that contains a root domain and two child domains. All servers run Windows Server 2008 R2. A corporate policy has the following requirements: èAll local guest accounts must be renamed and disabled. èAll local administrator accounts must be renamed. You need to recommend a solution that meets the requirements of the corporate policy. What should you recommend?()
- A、Implement a Group Policy object(GPO) for each domain.
- B、Implement a Group Policy object(GPO) for the root domain.
- C、Deploy Network Policy and Access Services(NPAS)on all domain controllers in each domain.
- D、Deploy Active Directory Rights Management Services(AD RMS)on the root domain controllers.
正确答案:A -
第21题:
多选题The network security policy requires that only one host be permitted to attach dynamically to each switch interfacE.If that policy is violated, the interface should shut down. Which two commands must the network administrator configure on the 2950 Catalyst switch to meet this policy? ()ASwitch1(config-if)# switchport port-security maximum 1
BSwitch1(config)# mac-address-table secure
CSwitch1(config)# access-list 10 permit ip host
DSwitch1(config-if)# switchport port-security violation shutdown
ESwitch1(config-if)# ip access-group 10
正确答案: D,C解析: 暂无解析 -
第22题:
多选题The network security policy requires that only one host be permitted to attach dynamically to each switch interface. If that policy is violated, the interface should shut down. Which two commands must the network administrator configure on the 2950 Catalyst switch to meet this policy (Choose two.)()。ASwitch1(config-if)# switchport port-security maximum 1
BSwitch1(config)# mac-address-table secure
CSwitch1(config)# access-list 10 permit ip host
DSwitch1(config-if)# switchport port-security violation shutdown
ESwitch1(config-if)# ip access-group 10
正确答案: E,A解析: 暂无解析 -
第23题:
单选题A network vulnerability scanner is part of which critical element of network and system security?()Ahost security
Bperimeter security
Csecurity monitoring
Dpolicy management
正确答案: A解析: 暂无解析
